Security Breach: PIX Scam Leads to Discovery of IDOR Vulnerability in Payment Gateway
Recently, one of our security analysts identified a critical IDOR (Insecure Direct Object Reference) vulnerability in a payment intermediary platform—this discovery came during an investigation into a scam involving alleged delivery issues by the postal service. This post details the fraud scenario, the investigation process, and the security risks found. The vulnerability is concerning and could have been exploited in large-scale scams.
Moises Cerqueira
4/29/20253 min read


### 🕵♂ The Scam: Fake Email + Payment Page
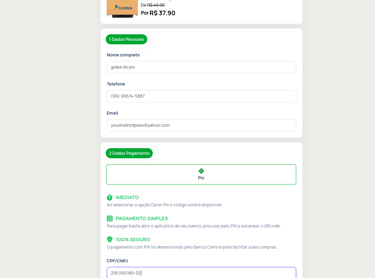
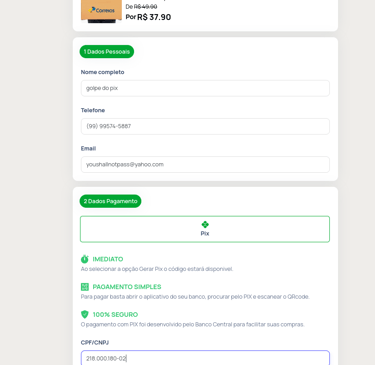
The attack begins with the delivery of fraudulent emails, claiming that a postal delivery was pending due to missing clearance. Upon clicking the link, the victim was redirected to a fake page requesting the following personal information:
- Full Name
- CPF ( Brazilian Taxpayer ID)
- Phone Number
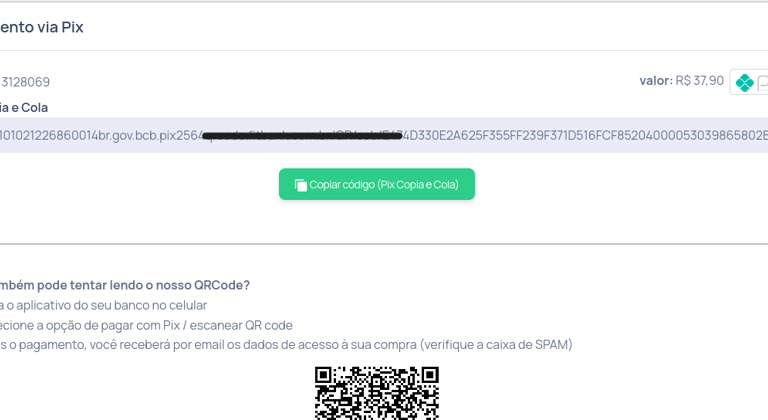
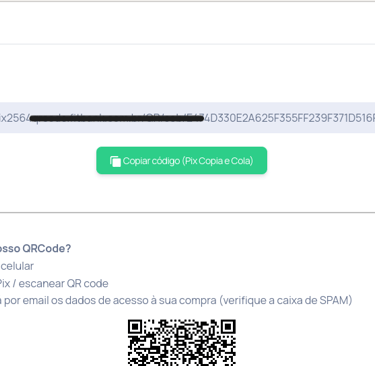
Next, the user was taken to a PIX payment code generation page—this time hosted on a legitimate domain belonging to a payment intermediary company.
---
### 🔍 Technical Investigation
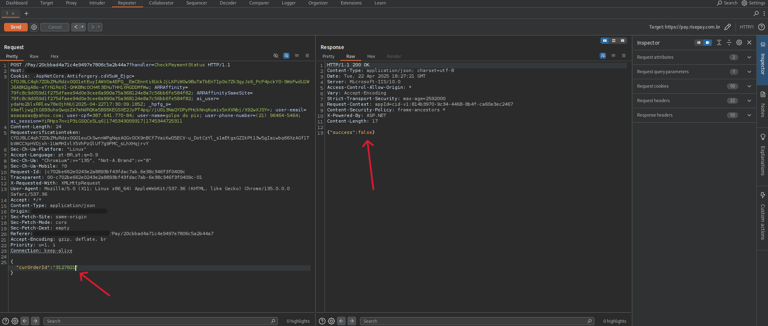
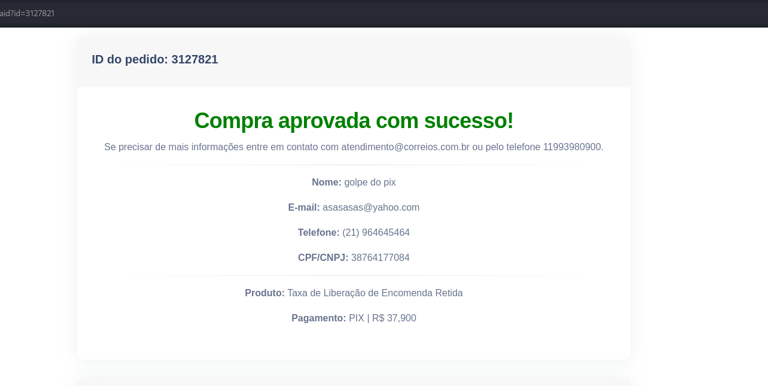
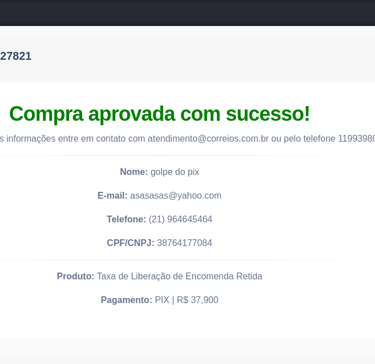
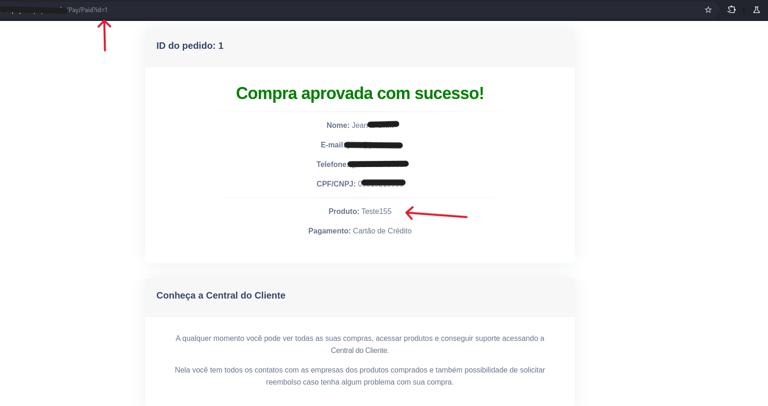
By analyzing the page requests using tools like Burp Suite, our analyst discovered that the system used POST requests to validate payments, relying solely on a numeric transaction ID.
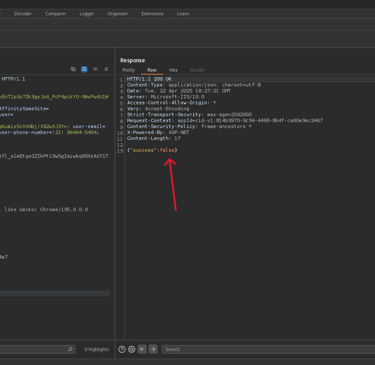
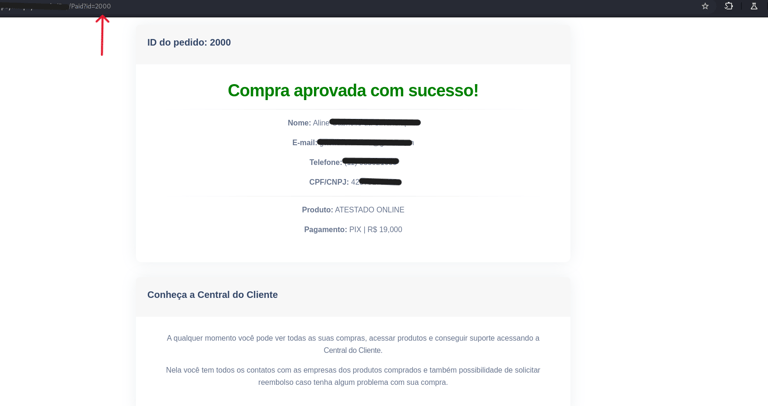
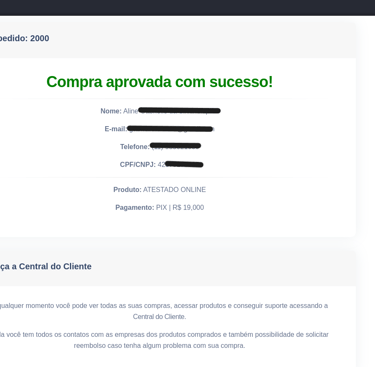
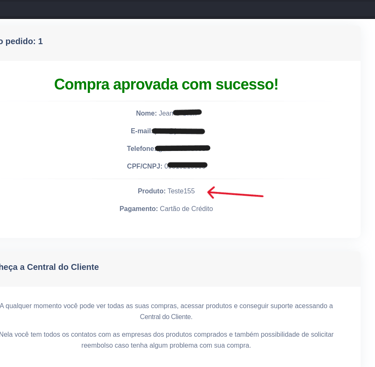
When modifying this ID to a low value (e.g., id=1), the system responded with "success:true"—indicating the transaction was marked as paid, even though no actual payment had been made.
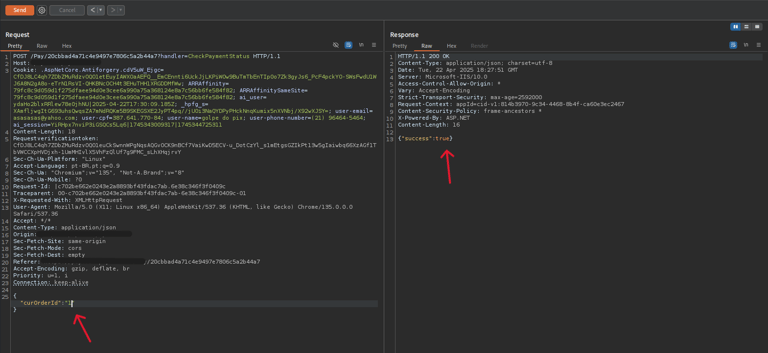
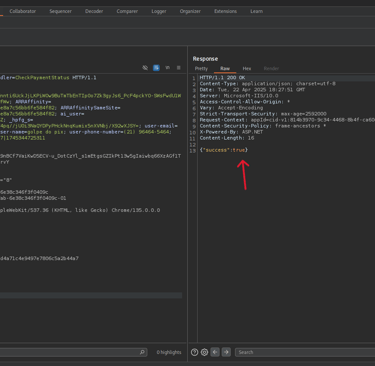
Furthermore, by manipulating the same ID in the confirmation URL, it was possible to access data from previous transactions. This exposed an IDOR (Insecure Direct Object Reference) vulnerability, where the system allows direct access to objects without properly verifying authentication or authorization.
---
### 🧨Identified Vulnerabilities
- Exposure of third-party data by modifying the id parameter
- IDOR (Insecure Direct Object Reference) vulnerability
- Endpoint /Pay/Paid exposed without authentication/authorization
- Direct violation of the General Data Protection Regulation (GDPR)
- Potential for large-scale abuse and fraud using the platform's infrastructure
---
### 🔎 Other Findings
During the scan, a publicly accessible staging instance of the platform was also found, hosted on Azure and indexed by Google — indicating that development/testing environments were exposed without proper protection.
---
### 📣 Real Impact
Further research revealed that the company has been mentioned in several public complaints, with reports of scams using its platform as a payment intermediary. So far, many victims claim they have not received a refund.
---
### 💬 Conclusion
This case demonstrates how a seemingly simple technical flaw can be exploited in complex fraud schemes with wide-reaching consequences. The lack of basic validations in payment systems can expose users and jeopardize the reputation of an entire company.
At Black Lotus Security, we continue to monitor, investigate, and disclose vulnerabilities that pose real risks to the digital ecosystem — with a focus on educating the public and improving the security of platforms.
---
Need help with fraud analysis, security testing, or incident response?
Get in touch with our team of experts.